Lab Information and Credentials
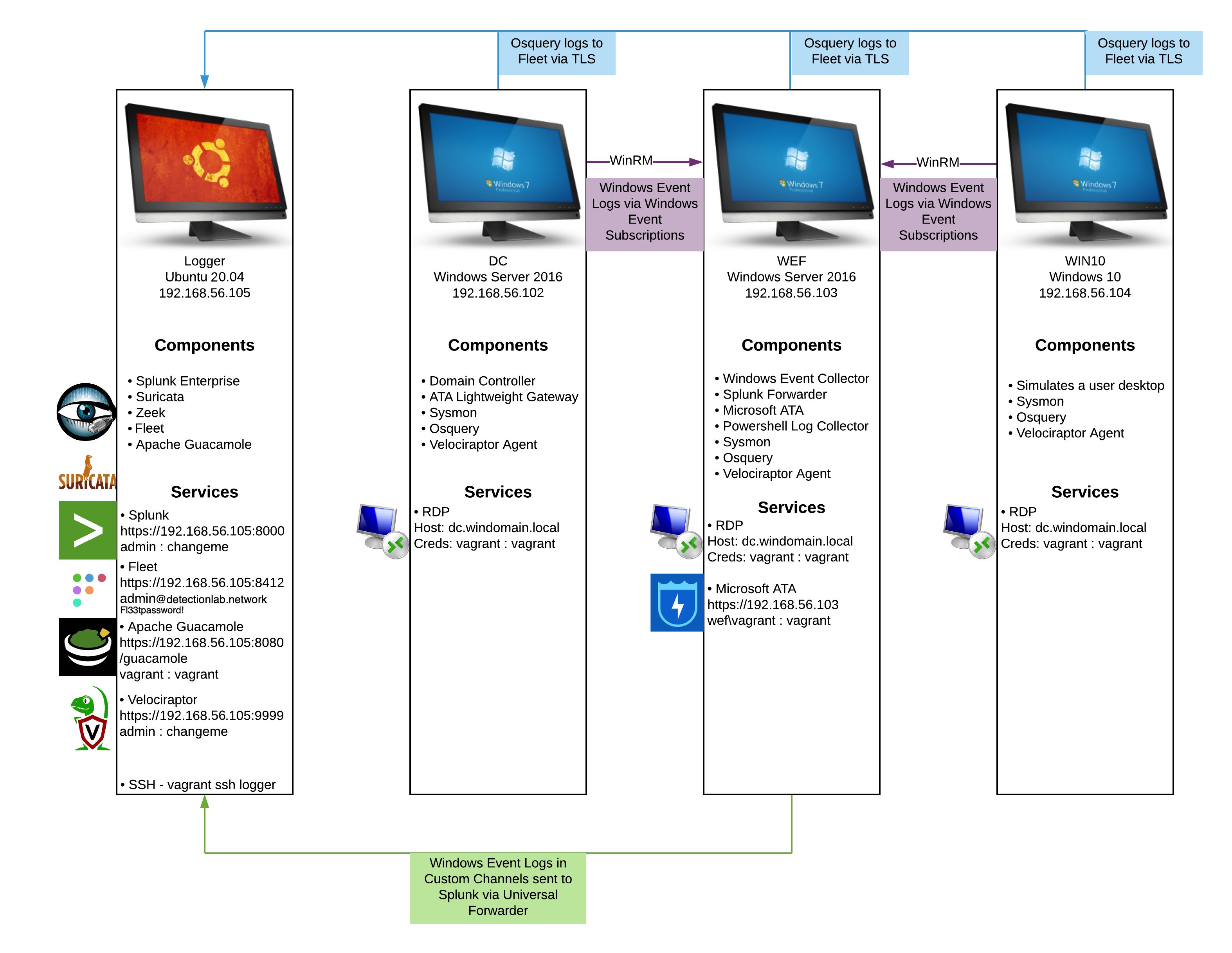
- Domain Name: windomain.local
- Admininstrator login: vagrant:vagrant
- Fleet login: https://192.168.56.105:8412 - admin@detectionlab.network:Fl33tpassword!
- Splunk login: https://192.168.56.105:8000 - admin:changeme
- MS ATA login: https://192.168.56.103 - wef\vagrant:vagrant
- Guacamole login: http://192.168.56.105:8080/guacamole - vagrant:vagrant
- Velociraptor login: https://192.168.56.105:9999 - admin:changeme
Lab Hosts
- DC - Windows 2016 Domain Controller
- WEF Server Configuration GPO
- Powershell logging GPO
- Enhanced Windows Auditing policy GPO
- Sysmon
- Velociraptor
- osquery
- Splunk Universal Forwarder (Forwards Sysmon & osquery)
- Sysinternals Tools
- Microsft Advanced Threat Analytics Lightweight Gateway
- WEF - Windows 2016 Server
- Microsoft Advanced Threat Analytics
- Windows Event Collector
- Windows Event Subscription Creation
- Powershell transcription logging share
- Sysmon
- Velociraptor
- osquery
- Splunk Universal Forwarder (Forwards WinEventLog & Powershell & Sysmon & osquery)
- Sysinternals tools
- Win10 - Windows 10 Workstation
- Simulates employee workstation
- Sysmon
- Velociraptor
- osquery
- Splunk Universal Forwarder (Forwards Sysmon & osquery)
- Sysinternals Tools
- Logger - Ubuntu 16.04
- Splunk Enterprise
- Fleet osquery Manager
- Zeek
- Suricata
- Guacamole
- Velociraptor server
Splunk Indexes
| Index Name | Description |
|---|---|
| evtx_attack_samples | Samples from https://github.com/sbousseaden/EVTX-ATTACK-SAMPLES |
| osquery | osquery/Fleet result logs |
| osquery-status | osquery/fleet INFO/WARN/ERROR logs |
| powershell | Powershell transcription logs |
| suricata | Suricata IDS logs |
| sysmon | Logs from the Sysmon service |
| threathunting | Used for the ThreatHunting app |
| wineventlog | Windows Event Logs |
| zeek | Zeek network traffic logs |
Installed Tools on Windows
- Sysmon
- Velociraptor Agent
- osquery
- AutorunsToWinEventLog
- Process Monitor
- Process Explorer
- PsExec
- TCPView
- Notepad++
- Google Chrome
- WinRar
- Mimikatz
- Wireshark
- Powersploit
- Atomic Red Team
- BadBlood